
Hard Disk Details(5)
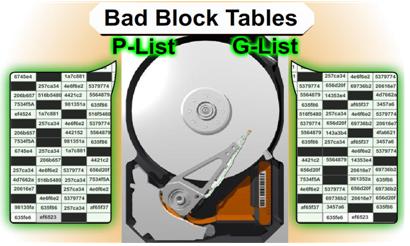
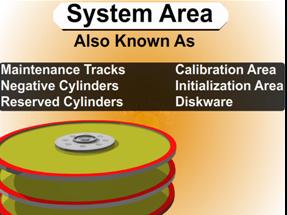
Slide 2221: When the drive is manufactured it is known that there is going to be errors in every drive. Drives use ECC to correct most errors and if ECC can correct the error then the sector is never marked as bad. If it is marked as bad, the drive puts the data in a bad block list. Most people know that their hard drive has a bad block table. What most people do not know is that their drive has TWO bad block tables.
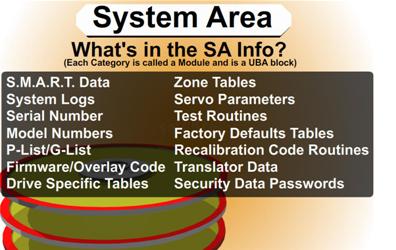
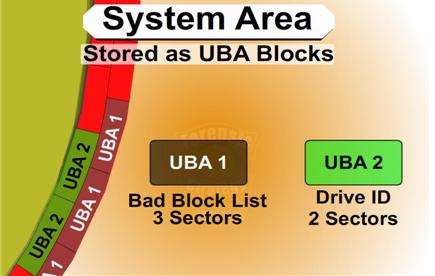
1. P-List (Primary Defects List – manufacture defect info that does not change)
2. G-List (Grown Defects Lists – sector relocation table)
The G-List is where the bad blocks that your drive has on a daily basis are stored. Since the P-List is done at manufacturing time that list is never suppose to change. There is a very important reason to know about both lists in a low level recovery which I will explain when we get to the repair section. There are certain utilities that can read, delete, merge and change this data.
ECC Notes and Issues
ECC structured redundancy up to 200 bits of 256/512 in a sector-CRC–Scrambled Bits- RLL adds bits to cause pulses and Parity When data is written to the drive it is encoded. The actual data itself is never written, only the interpretation of the data. If you are thinking that a drive contains 0’s and 1’s then you are thinking about it incorrectly. The data is more like a wave form being written to the drive. It has to be interpreted back on its way out before it becomes a 0 or a 1. Before the data is written the data is randomized. This eliminates patterns that might be the same so that ECC is not confused. It is difficult to do pattern detection on a pattern that appears over and over. EMI can be reduced and have less effect on the bit storage and the timing controls.
The drive tries several different ways to re-read the data before giving up, most of them using ECC. It is possible for ECC to improperly correct data under certain circumstances if the data occurs in a certain order. ECC read commands use ODD numbering of at least 3 so as not to cause a 50/50 chance in the selection of 2.
Read ignoring ECC is an LBA 28 command “Read Long” and it was disabled in 48 bits as it was determined to be obsolete in drives over 137 gigs. No Read Ignore ECC is available after 137 gigs. Standard attempts are tried and usually are 10 tries in most hard drives. Reading a drive ignoring ECC can cause possible corruption in the data, but sometimes it is the only way to get the data in those sectors if there is a problem with the PCB or the ECC cannot read the data correctly.
If the Sector is determined to be unreadable by the ECC encoder then the sector is retried again. Reed Solomon in conjunction with sector rereads is expecting to fix data errors for the ECC. Parity bits are stripped off.
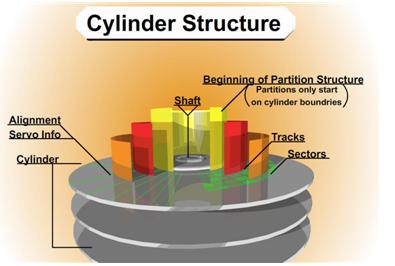
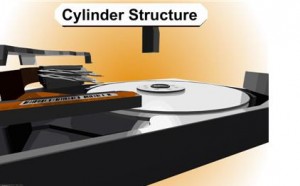
Slide 2422: The cylinder structure is extremely important because there are people believe they can just take the platters out and move them to a new drive. This is true you can do this, but you have to move all platters simultaneously. The reason is because data is written in a cylinder. Most people have heard the term cylinder in reference to their hard drive, but they have no idea what that means. Writing in a cylinder means that data is written in parallel due to the fact the heads are always moving together in the same stack. To make it more efficient data is written on the top of a platter and the bottom of the platter and the next platters and so on, at the same time. Your data is NOT written on the top of one platter and when that gets full then written to the next platter. It is written across all the platters at the same time, making a cylinder of your data.
Most data recovery software will scan an entire hard drive and then display a list of files and directory trees you can recover from. However, if there is a lot of damage to the drive, the scanning may never finish or it might die/kill it in the process. If you have smart software and you can figure out where your partitions start and where the MFT or FAT tables might be, you stand a better chance of getting the data you are looking for. If a standard utility was used to create the partition then the partition structure will begin on a cylinder boundary. Again, your partition will begin on a Cylinder Boundary. Software like Byteback (www.byteback.org) RecoverSoft Media Tools Pro (www.recoversoft.com), and Runtimes Disk Explorer (www.runtime.org) are smart enough to know the data exists on the cylinder boundary and will quickly check without you have to scan the whole hard drive and possibly saving your drive from disaster during the scan. There certainly are times that scanning will be required but it is best if you can avoid it except in an imaging process.
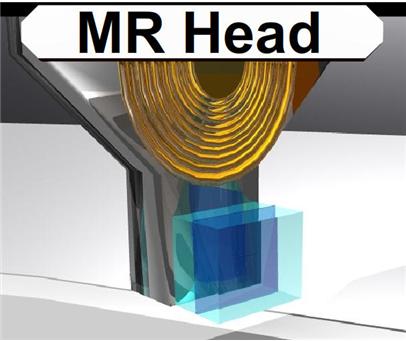
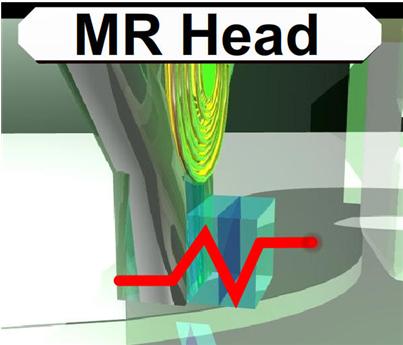
Slide 2585: The MR (magnetoresistive) head of the hard drive you can think of as the head of the 90’s. If you remember how reliable the drives were before 2000 it is mostly because of this head and the density of the platters. This head was used on drives mostly before we crossed the 10-20 gig barriers. The MR head could determine if a bit passed under it. When data passed parallel to the head, the head could detect the “MR Effect” due to movement of electrons causing the magnetic field to rotate positive and negative values.





 MacLockPick™ is a valuable tool for law enforcement professionals to perform live forensics on Mac OS X systems. The solution is based on a USB Flash drive that can be inserted into a suspect’s Mac OS X computer that is running (or sleeping). Once the software is run it will extract data from the Apple Keychain and system settings in order to provide the examiner fast access to the suspect’s critical information with as little interaction or trace as possible. And also this is the only professional tool which can be use to extract the extensive encrypt information under the close-down condition of computer.
MacLockPick™ is a valuable tool for law enforcement professionals to perform live forensics on Mac OS X systems. The solution is based on a USB Flash drive that can be inserted into a suspect’s Mac OS X computer that is running (or sleeping). Once the software is run it will extract data from the Apple Keychain and system settings in order to provide the examiner fast access to the suspect’s critical information with as little interaction or trace as possible. And also this is the only professional tool which can be use to extract the extensive encrypt information under the close-down condition of computer.