When we are coming to the topic of flash data recovery, it’s very necessary for us to have a general view of the typical failures of flash drives such as the SD, CF, SM ,MMC, XD, USB Pendrive, MemoryStick, etc.
It’s believed 90% of flash drives’ failures are due to corruption in the lookup tables which convert logical addresses (what your computer sees) to physical addresses (what the controller sees). Other failures are usually caused by controller failures, power surges, and worn or broken solder joints.
NAND memory has many quarks.
* Each block is only good for a finite number of writes after which bit errors occur, for example the word “flash” may become “slash”.
* Data can be read in pages (2K bytes) but must be written in blocks (128K bytes).
* Before a write can occur the block must be erased, if power is lost before a write completes the sector remains erased.
Lookup tables
Lookup table is an array or matrix of data that contains items that are searched. Lookup tables may be arranged as key-value pairs, where the keys are the data items being searched (looked up) and the values are either the actual data or pointers to where the data are located. Sometimes, lookup tables contain only data items (just values, not key-value pairs).
Each word (two bytes) contains the block number which holds that sectors data. For example 0×001A is the block number for sector 0, 0×0419 is the block number for sector 1, etc. If the block numbers are incorrect the controller won’t know where the actual data is stored. In this example some of the block numbers are incorrect because of bit errors caused by an aging NAND chip. Some controllers may automatically detect the error and prevent further writes. In this case the user may get an error message asking them to format the drive.
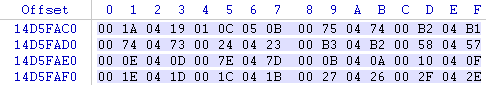
In this example the flash drive was unplugged before a write operation on the lookup table completed leaving the table filled with 0xFFFF from the erase cycle. The user may be prompted to insert removable media, the drive may be displayed as 0MB in size, if the drive is listed it may be shown as an unknown device.
As NAND memory ages bits inside a block can become stuck, newer high density MLC chips are plagued by this problem. To combat this controller manufactures use ECC (Error Correcting Code) to fix a limited number of bit errors. Once the number of correctable bits per sector is exceeded flash drives may act strangely for example frequent file system corruption may occur or the drive will stop working. In these cases I’ll often see color shift in pictures, half the image will be normal and the other half will be a different tint. This is because part of the image was stored in a good block while the other part was in a bad block with sticky bits.
Weak Solder Joints
Wear and tear on the drive can cause solder joints on the NAND memory chip or controller to weaken. If the drive is recognized the total capacity will only be a few megabytes. If you connect the drive while applying LIGHT PRESSURE to the controller and NAND memory you may be able to retrieve the data. Remember, weak solder joints account for LESS THAN 10% of failures. DON’T APPLY MORE PRESSURE if this doesn’t work, you may damage the NAND memory chip if you press too hard.
Hacked USB Flash Drives
Some unbranded or counterfeit flash drives are hacked to display the wrong drive size using the manufactures mass production tool and then sold as larger capacity drives. For example a flash drive with a 4GB NAND chip will report itself as 8GB drive. These drives often work until the user starts to fill the drive with data after which it becomes unreadable. These fake flash drives are usually sourced from china and sold on eBay. If your data is NOT important you can download the mass production tool for the drives controller and reformat the drive using the correct capacity.
Broken USB Connector
If the USB connector was broken off the USB Flash drive you can recover the data by repairing the trace using a conductive pen.
1. Use a set of tweezers to place whats left of the trace on its original path
2. Expose the copper at the end of the broken trace by scraping off the sealant with an XACTO knife
3. Use a conductive solder pen (available online or at radio shack) and carefully recreate the broken trace.
4. Let the paste dry, then use a needle or XACTO knife to scrape off any excess.
5. Make sure the trace is repaired by doing a continuity test with a multi-meter from the pad to the end of the trace.
6. Quickly solder the old USB connector back on the board. The paste left by the pen won’t hold up to heat for very long, don’t spend too much time trying to make the joint perfect.
7. CAREFULLY connect the flash drive to your computer, the connection is VERY weak and easily broken. I recommend connecting the drive to a USB extension cable for easier insertion.
Bad Surface Mounts
Leaving a flash drive plugged constantly in may cause premature failure of the surface mounts which regulate voltage to the flash drive’s components. Often the resistance or capacitance values of a surface mount will fall out of spec and not produce the correct voltage. This often represents itself as a dead flash drive (no led, not acknowledge by the computer) or overheating.
As for flash data Recovery, the NAND memory chip must be removed and read with an external reader, then the lookup table is reconstructed to retrieve your data.
As for flash data recovery tools, there are not many good ones to recommend, so far ACE flash data recovery tool and the coming flash doctor can be worth a try. There are many data recovery providers who have their own tools for this kind of recovery, but according to customers, the result is not ideal!




 /etc/crontab
/etc/crontab