 –profile
–profile
–System wide environment and startup script program.
/dev/MAKEDEV
The /dev/MAKEDEV file is a script written by the system administrator that creates local only device files or links such as device files for a non-standard device driver.
/etc/aliases
Where the user’s name is matched to a nickname for e-mail.
/etc/bootptab
The configuration for the BOOTP server daemon.
/etc/crontab
Lists commands and times to run them for the cron deamon.
/etc/dhcpd.conf
The configuration file for the DHCP server daemon.
/etc/ethers
File for RARP mapping from hardware addresses to IP addresses. See the man page ethers(5).
/etc/exports
The file describing exported filesystems for NFS services.
/etc/fdprm
The floppy disk parameter table. Describes the formats of different floppy disks. Used by setfdprm.
/etc/filesystems
Can be used to set the filesystem probe order when filesystems are mounted with the auto option. The nodev parameter is specified for filesystems that are not really locally mounted systems such as proc, devpts, and nfs systems.
/etc/fstab
Lists the filesystems mounted automatically at startup by the mount -a command (in /etc/rc or equivalent startup file).
/etc/group
Similar to /etc/passwd but for groups rather than users.
/etc/groups
May contain passwords that let a user join a group.
/etc/gshadow
Used to hold the group password and group administrator password information for shadow passwords.
/etc/host.conf
Specifies how host names are resolved.
/etc/hosts
List hosts for name lookup use that are locally required.
/etc/HOSTNAME
Shows the host name of this host. Used for support of older programs since the hostname is stored in the /etc/sysconfig/network file.
/etc/inittab
Configuration file for init, controls startup run levels, determines scripts to start with.
/etc/inetd.conf
Sets up the services that run under the inetd daemon.
/etc/issue
Output by getty before the login prompt. Description or welcoming message.
/etc/issue.net
Output for network logins with LINUX version
/etc/ld.so.conf
Configuration file for ld.so, the run time linker.
/etc/lilo.conf
Configuration file for LILO.
/etc/limits
Limits users resources when a system has shadow passwords installed.
/etc/localtime
In Debian the system time zone is determined by this link.
/etc/login.defs
Sets user login features on systems with shadow passwords.
/etc/logrotate.conf
Configures the logrotate program used for managing logfiles.
/etc/magic
The configuration file for file types. Contains the descriptions of various file formats for the file command.
/etc/motd
The message of the day, automatically output by a successful login.
/etc/mtab
A list of currently mounted file systems. Setup by boot scripts and updated by the mount command.
/etc/named.conf
Used for domain name servers.
/etc/networks
Lists names and addresses of your own and other networks, used by the route command.
/etc/nologin
If this file exists, non-root logins are disabled. Typically it is created when the system is shutting down.
/etc/nsswitch.conf
Name service switch configuration file.
/etc/passwd
The user database with fields giving the username, real name, home directory, encrypted password and other information about each user.
/etc/printcap
A configuration file for printers.
/etc/profile, /etc/cshlogin,/etc/csh/cshrc
Files executed at login or startup time by the Bourne or C shells. These allow the system administrator to set global defaults for all users.
/etc/protocols
Describes DARPA internet protocols available from the TCP/IP subsystem. Maps protocol ID numbers to protocol names.
/etc/rc or /etc/rc.d or /etc/rc?.d
Scripts or directories of scripts to run at startup or when changing run level.
/etc/rc.d/rc0.d
Contains files used to control run level 0. Usually these files are softlink files.
/etc/rc.d/rc1.d
Contains files to control run level 1. Scripts beginning with an S are for start, K for kill.
/etc/rc.d/rc.sysinit
Init runs this when it starts.
/etc/resolv.conf
Configures the name resolver, specifying the address of your name server and your domain name.
/etc/securetty
Identifies secure terminals from which root is allowed to log in.
/etc/services
Lists the network services that the system supports.
/etc/shadow
Shadow password file on systems with shadow password software installed. Shadow passwords move the encrypted password files from /etc/passwd to /etc/shadow which can only be read by root.
/etc/shadow.group
Systems with shadow passwords may have this file.
/etc/shells
Lists trusted shells. The chsh command allows users to change their login shell to shells listed only in this file.
/etc/skel/.profile
Can be used by administrator to set the editor environment variable to some editor that is friendly to new users.
/etc/sudoers
A list of users with special privileges along with the commands they can execute.
/etc/smb.conf
The configuration file for setting up Samba services.
/etc/sysconfig/amd
Used to configure the auto mount daemon.
/etc/sysconfig/clock
Used to configure the system clock to Universal or local time and set some other clock parameters.
/etc/sysconfig/i18n
Controls the system font settings.
/etc/sysconfig/init
This file is used to set some terminal characteristics and environment variables.
/etc/sysconfig/keyboard
Used to configure the keyboard.
/etc/sysconfig/mouse
This file is used to configure the mouse.
/etc/sysconfig/network-scripts/ifcfg-interface
Defines a network interface.
/etc/sysconfig/pcmcia
Used to configure pcmcia network cards.
/etc/sysconfig//routed
Sets up dynamic routing policies.
/etc/sysconfig/static-routes
Configures static routes on a network.
/etc/sysconfig/tape
Used for backup tape device configuration.
/etc/X11/XF86Config
The configuration file for the X server.
/etc/syslog.conf
Configuration file for the syslogd daemon.
/etc/termcap
The terminal capability database. Describes by what “escape sequences” various terminals can be controlled. See terminfo, termcap, curs_termcap man pages.
/etc/terminfo
Details for terminal I/O.
/etc/usertty
This file is used to impose special access restrictions on users.
$HOME/.bashrc
User aliases, path modifier, and functions.
$HOME/.bash_profile
Users environment stuff and startup programs.
$HOME/.bash_logout
User actions to be done at logout.
$HOME/.hushlogin
When this file exists in the user’s home directory, it will prevent check for mail, printing of the last login time, and the message of the day when the user logs in.
$HOME/.inputrc
Contains keybindings and other bits.
$HOME/Xrootenv.0
Has networking and environment info.
/proc/cpuinfo
Information about the processor such as its type, make and performance.
/proc/devices
A list of devices configured into the currently running kernel.
/proc/dma
Shows which DMA channels are being used at the moment.
/proc/filesystems
Filesystems that are configured into the kernel. The file used to detect filesystems if the /etc/filesystems does not exist.
/proc/ioports
Shows which I/O ports are in use at the moment.
/proc/interrupts
Shows which interrupts are in use and how many of each there have been.
/proc/kcore
An image of the physical memory of the system.
/proc/kmsg
Messages output by the kernel. These are also routed to syslog.
/proc/ksyms
Symbol table for the kernel.
/proc/loadavg
The load average of the system.
/proc/meminfo
Information about memory usage, both physical and swap.
/proc/modules
Which kernel modules are currently loaded.
/proc/mounts
Contains information on filesystems currently mounted, similar to /etc/mtab
/proc/net
Contains status information about network protocols.
/proc/self
A symbolic link to the process directory of the program that is looking at /proc. When 2 process look at proc, they get different links.
/proc/stat
Various statistics about the system such as the number of page faults since the system was booted.
/proc/uptime
The time the system has been up.
/proc/version
The kernel version.
/tmp/fvwmrca01339
FVWM-M4 defines. Contains networking, Xwindows, other setup info.
/usr/lib/zoneinfo
Time zone datafiles are stored here on the Debian system
/var/log/lastlog
Used by finger to tell when a user was last logged in.
/var/log/wtmp
Binary info on users that have been logged on. The last command uses this info.
/var/run/utmp
Contains information about users currently logged in. Who and w commands use this file.
/var/named/root.hints
Used for domain name server. Placed here optionally, but this is the normal location.
/var/named/*
Files used by domain name server. Placed here optionally, but this is the normal location.
/var/log/btmp
Used to store information about failed logins. This file must be first created to activate it.
/var/log/lastlog
Contains information about the last time a login was done on the system. Works with lastb(1).
/var/log/maillog
The normal system mail log file.
/var/log/messages
The main system message log file.
var/log/secure
System tracking of user logins. Check this file periodically.
/var/spool/mail
Where mailboxes are usually stored.

 1. Stellar Phoenix Macintosh Data Recovery Software
1. Stellar Phoenix Macintosh Data Recovery Software
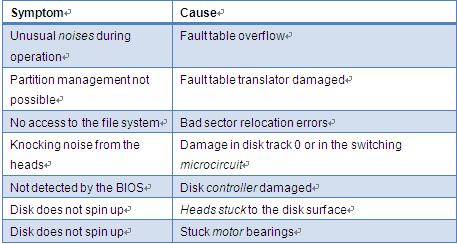
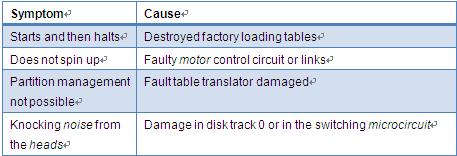
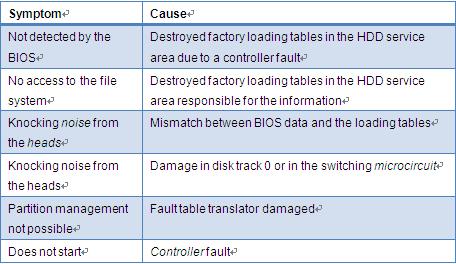
 Information technology is at the core of almost every organization today. The computer data is one of the invaluable assets for a company. Any computer related disaster can result in irreversible losses for the company. To avoid such disasters out of the blue most companies have a disaster recovery planning as a part of a business continuity planning. To over this important for every organization, you should plan a disaster recovery using with the help of disaster recovery tool. Disaster recovery tools are essentially a part of Disaster Recovery Planning (DRP). The DRP documents chalk out the plan of action prior to, during and following a disaster. The DRP helps a business to minimize its losses caused by a system crash and helps it to recover from a disaster in the shortest possible time by identifying critical systems, processes and methods for restoring the processes.
Information technology is at the core of almost every organization today. The computer data is one of the invaluable assets for a company. Any computer related disaster can result in irreversible losses for the company. To avoid such disasters out of the blue most companies have a disaster recovery planning as a part of a business continuity planning. To over this important for every organization, you should plan a disaster recovery using with the help of disaster recovery tool. Disaster recovery tools are essentially a part of Disaster Recovery Planning (DRP). The DRP documents chalk out the plan of action prior to, during and following a disaster. The DRP helps a business to minimize its losses caused by a system crash and helps it to recover from a disaster in the shortest possible time by identifying critical systems, processes and methods for restoring the processes.
 –profile
–profile